Tailored Security, Continuous Evolution
We Protect Your Business to Guide It into the Digital Future
We Protect Your Business with a Tailored Approach, Ready for Digital Challenges
Cybersecurity is not a one-time solution, but a continuous journey.
Our Iterative and Incremental Approach Adapts to Your Business Evolutions and Emerging Digital Threats.
Understanding your business in depth is the first step to offering you effective and personalized solutions. We focus on mapping business processes, integrating cybersecurity management to ensure operational continuity and protection. We prevent threats and enhance the security of your processes, allowing your company to operate safely, reliably, and without interruptions.

Comprehensive Protection, Forward-Looking Vision
Our approach to security goes beyond solving existing problems; it aims to prevent and mitigate future risks through a personalized and proactive strategy. We offer an integrated method based on in-depth vulnerability analysis, continuous risk management, and constant monitoring. Our goal is to ensure maximum protection for your business, anticipating threats and building digital resilience, allowing you to focus on developing your activities with security as a solid foundation.
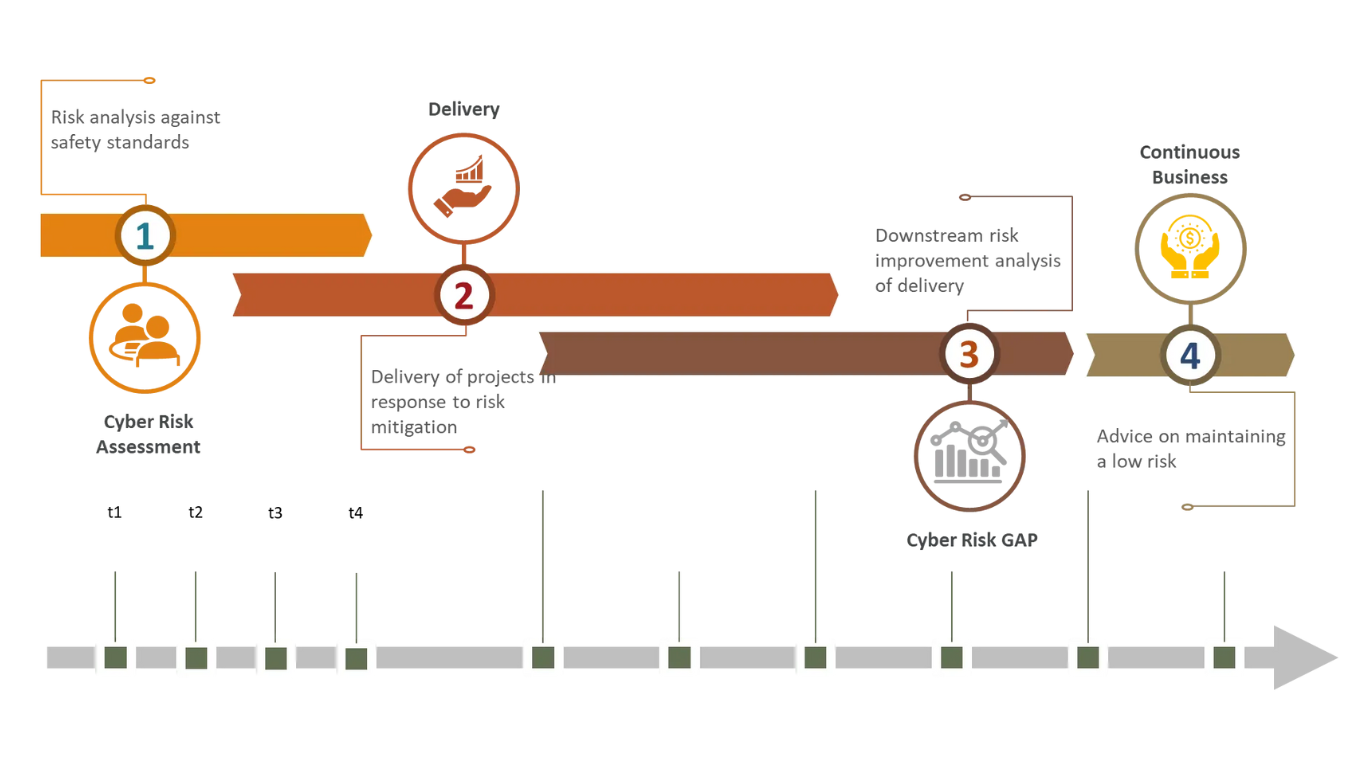
An Iterative and Incremental Design Approach Based on 4 Steps
STEP 1
CYBER RISK ASSESSMENT
We thoroughly analyze the cybersecurity risks your organization faces. Through this assessment, we help you better understand vulnerabilities and potential risks, providing the necessary information to make informed decisions and develop effective mitigation strategies.
STEP 2
DELIVERY
In this phase, we implement practical solutions to reduce or manage the identified risks. This is when we turn theory into action, ensuring that security measures are tailored to the specific needs of your company.
STEP 3
Cyber risk gap
After the implementation phase, we analyze opportunities for risk improvement. We verify that the adopted measures have addressed the identified gaps and propose further actions to enhance security.
STEP 4
continuous business & EDUCATION
Cybersecurity doesn’t end with implementation. We continuously monitor your system, ready to detect and respond promptly to any attack or security breach, ensuring constant and lasting protection.
Four Steps to Security
Our integrated approach ensures that your company tackles today’s threats and is prepared for tomorrow’s opportunities, while always maintaining high operational efficiency.